Even before the pandemic forced workplaces into the cloud, collaboration tools were popular among employees. For years now, apps like Microsoft Teams and Slack have helped teams streamline their workflows, keeping employees from spending hours a week hunting down data or unnecessarily repeating their work.
But the same collaboration tools that employees love often present security threats to the companies they work for.
According to Skyhigh Security, less than 10 percent of the cloud-based apps most commonly used by enterprises meet enterprise security and privacy requirements. And that lack of security has very real costs for businesses: according to IBM, the average cost of a data breach hit $9.44 million in the United States this year. These breaches are no longer rare occurrences, either: 70 percent of organizations hosting data in the public cloud say they’ve experienced a security incident in the last year.
Everybody wants to increase collaboration and communication at work — but that shouldn’t come at the cost of data security. Below, we’ll explain exactly what to look out for when judging an app’s security, then share a few of our favorite secure collaboration tools that increase productivity… without giving any IT teams a heart attack.
How can you tell if an app is secure?
A good place to start when evaluating a tool’s security is to think about security risks. According to G2, the most common security threats presented by software are data breaches, identity theft, insider threats, and phishing.
Below, we’ll explain what each threat entails, and the specific features you should look for to keep them at bay.
Data breaches & identity theft
When a data breach occurs, unauthorized third parties gain access to your company or your client’s confidential information. This usually occurs when hackers find vulnerabilities in your security systems. If hackers are able to access clients’ or employees’ personal information in these breaches, identity theft becomes a risk.
Data encryption is generally the first line of defense against data breaches. When data is encrypted, it’s essentially illegible unless the person accessing the data has the right “key” to decipher the encrypted information. So even if hackers exploit a vulnerability in your security systems, they’ll have a hard time accessing sensitive information if it’s encrypted.
Insider threats
Unfortunately, not all of the threats to your company’s security are external. In 2021, 94 percent of organizations experienced insider data breaches: the access of data by current or former employees, contractors, vendors, or business partners who have been granted access to an organization’s systems. Most of the time, this access takes place accidentally rather than maliciously. For instance, the company may forget to revoke a former team member’s access to a tool when they leave their role, or a contractor may be granted access to a full folder (rather than a single file).
To protect against insider threats, apps should have varying privacy permissions to allow different users access to levels of data. It can also be smart to see if a tool lets users log in using single sign-on (SSO), which lets a company control users’ access to multiple tools through a single login. That way, if an employee leaves the company, the company only needs to revoke their access to one tool — rather than the hundreds that most companies use.
Phishing
A phishing attempt takes place when a third party tricks an authorized user into sharing sensitive information with them. For instance, a phishing email may convince one of your employees to share their login information to an app by sending a realistic-looking “Reset your password” email.
Since there’s a human element to phishing, it can be hard to stop altogether. However, two-factor authentication (2FA) can help ensure that even if a malevolent actor gains access to an employee’s login information, they’re still met with another layer of protection. With 2FA in place, users need to provide two methods of authentication when they log into a service — for instance, a user may enter their credentials when logging in, then need to confirm their identity by clicking a link sent to their email. Some single sign-on providers will also offer 2FA.
Five secure collaboration platforms
Whether you’re just starting to look into collaboration tools or you’re realizing that — whoops! — a few of your current apps don’t quite meet your security requirements, not to worry. We’ve outlined five of our favorite secure collaboration tools that are user-friendly, yet secure.
1. GoLinks
The average enterprise uses a total of 1,295 cloud apps across their company, making it difficult — if not downright impossible — for team members to know where certain resources are stored. Is it any wonder, then, that the average employee spends 3.6 hours a day simply looking for information?
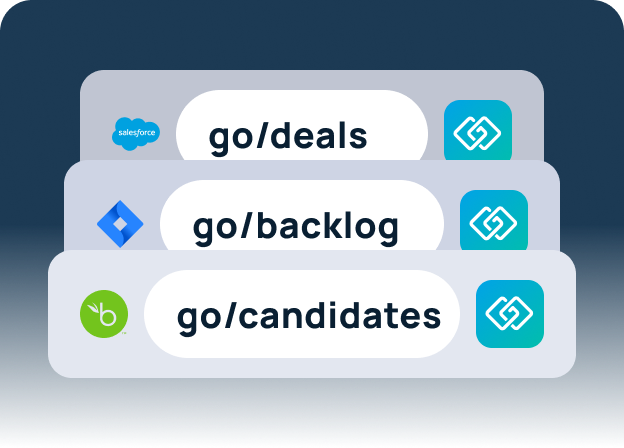
GoLinks (that’s us!) is a team collaboration app that aims to change that. GoLinks allows your teams to find and share information by using intuitive, memorable short links. For instance, your product team might create a short link to their product roadmap in Jira and name it simply “go/roadmap.” The HR team may link to their onboarding guide in Microsoft Office using the short link “go/onboarding.” If anyone at the company plugs either of those go links into their browsers, they’ll be redirected to the appropriate resource.
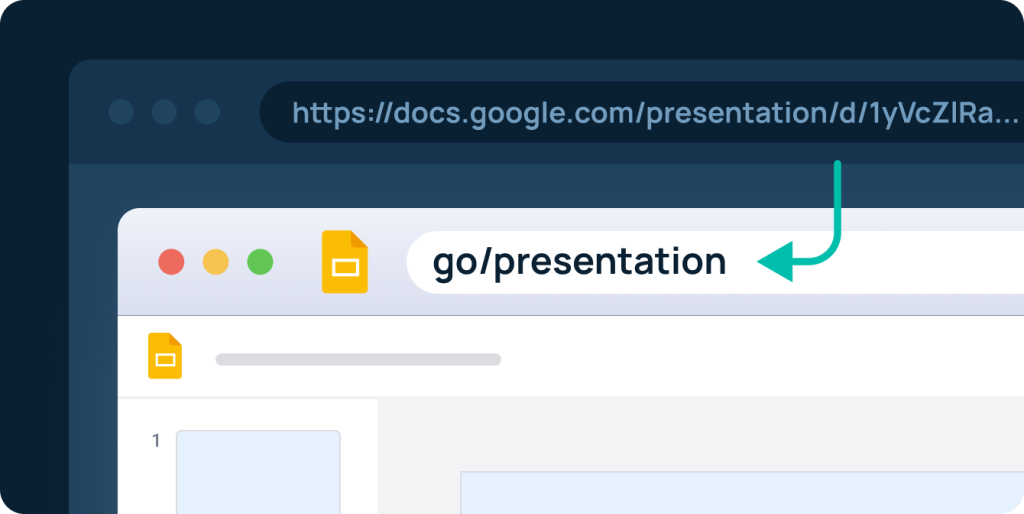
GoLinks not only saves teams hours a day, but it allows for secure file sharing thanks to its robust security features:
- Single sign-on makes it easy for administrators to grant and revoke employees’ access to the tool at a single click. SSO also provides protection against phishing, since employees with SSO in place don’t need to use a dedicated username and password to access GoLinks.
- Full admin controls allow you to set permissions at the workspace, admin, and member level — so everyone has access to exactly what they need and nothing more.
- Access logs track every time a user logs into your GoLinks instance, so that you have a trail of bread crumbs to follow in the event of an internal breach.
- 2048 bit SSL encryption keeps data encrypted in transit and at rest to combat data breaches.
- SOC 2 certification means GoLinks has been audited and met the trust, privacy, and security criteria for the American Institute of Certified Public Accountants (AICPA) — a certification that only 18 percent of the top 1,000 software apps today have acquired.
On top of that, GoLinks has a 99.9% uptime Service Level Agreement (SLA) — which means that we guarantee GoLinks will be up and running 99.9% of the time. It also plays really, really well with other collaboration tools (including those listed below!), helping employees keep resources, task lists, and projects on hand and organized.
2. Slack
At this stage, Slack’s notification sound has come to be nearly synonymous with corporate communication — and for good reason. Slack allows in-office and remote employees to centralize and preserve their real-time communication, with options for private, public, and topic-specific messaging. Companies can create shared Slack channels with their clients or contractors, and a search bar makes it easy for employees to find the messages, photos, and resources they need in Slack.
Considering that it acts as many companies’ main hub for online collaboration, Slack meets stringent security standards and offers:
- Single sign-on to manage employee access to the app and lower phishing risks.
- Two-factor authentication that provides extra protection from phishing.
- Strict admin controls and the ability to manage permissions for each workspace channel.
- SOC 2, SOC 3, and ISO IEC 27001 certification, among other industry-leading certifications.
- Data encryption in transit and at rest to protect clients from data loss and breaches.
- Audit logs keep track of all activity in Slack, helping admins protect against insider threats.
3. BaseCamp
BaseCamp is a flexible project management tool that lets teams centralize resources, create to-do lists, schedule tasks, and share feedback. Individuals and teams can create BaseCamp boards to organize their projects, teams, or day-to-day work.

Teams upload plenty of proprietary data and client information to their boards, so keeping data secure is a priority for the Basecamp team. According to Basecamp, the project management platform has never had a data breach. Some of the security features they have in place include:
- Data encryption in transit and at rest.
- A safety monitoring team that maintains clients accounts’ security on Basecamp systems.
- A public bug bounty program that pays security researchers to find and report any potential security risks.
4. Asana
Asana is another heavy-hitter in the project management world. Teams organize projects and manage work in Asana, and they can use Asana’s rules, forms, and templates to automate any routine work. Individuals can also toggle between different project views, letting them visualize their work in a way that works best for them.

To keep client data protected, Asana offers users:
- Single sign-on and two-factor authentication to reduce phishing and data breach risks.
- Admin controls allow companies to set granular permissions at the user, task, and project level.
- Enterprise Key Management lets enterprises use their own encryption key for any data stored in Asana.
- SOC 2, SOC 3, and more certifications that ensure Asana meets external standards for trust and security.
- Audit logs let enterprise administrators detect and track security threats.
5. Trello
Last but certainly not least, Trello is a work management tool that lets teams visualize and track their work. Trello users can organize work in Kanban boards, calendars, timelines, tables, and dashboards, and teams can set up automation rules that cut down on repetitive work.
To protect clients’ data, Trello boasts the following security features:
- Single sign-on to protect companies from inside threats and phishing.
- Data encryption in transit and at rest.
- SOC 2 and ISO/IEC 27001 certification that validates Trello’s trust and security controls.
- A bug bounty program encourages security researchers to find and report any vulnerabilities in Trello’s security for a reward.
- Admin controls let administrators set granular permissions for users, allowing them to control who has access to what.
Get collaborative — safely
Collaboration tools can help boost your teams’ productivity, innovation, and morale — but none of those things should come at the expense of your organization’s safety. By adopting secure collaboration tools, you can get the best of both worlds. Best of all, GoLinks integrates with all of the tools listed above and more — so you can use multiple tools to safely increase collaboration at work.
Ready to dive in? Start building your secure collaboration stack with a free trial of GoLinks.
Access and share resources instantly with GoLinks
Try for free